GNSS spoofing: a fatal attack on GNSS system that is difficult to detect
Global navigation satellite system (GNSS), such as the infamous global positioning system (GPS), can provide position, velocity and timing (PNT) solutions in global scale and is mostly free to use by people with, for example, a smartphone at hand or any low-cost GNSS receiver.
Global navigation satellite system (GNSS), such as the infamous global positioning system (GPS), can provide position, velocity and timing (PNT) solutions in global scale and is mostly free to use by people with, for example, a smartphone at hand or any low-cost GNSS receiver.
Timing solutions for synchronisation provided by GNSS system have vital roles in many daily-life applications. For examples, power grid system, automatic stock trading system, financial transaction timestamp and cell phone tower system rely on precision timing provided by GNSS system.
However, since the signals of GNSS are from medium-earth-orbit satellites far above the earth (approximately 23000 km above the earth), the GNSS signals received on earth are very weak. The power of GNSS signal received by a receiver on earth is approximately -130 dBm.
For intuition how weak a -130 dBm GNSS signal is, we can think of it as a 25 W lightbulb that is seen from around 16000 km away [2].
In addition, most GNSS solutions use by public are those that are an open protocol (known message bit structure, known signal processing steps, no encryption, etc) where any receiver can process and interpret the signals. This open protocol system can be manipulated and re-broadcasted using low-cost transmitters. Although, new GNSS signals are equipped with cryptographic features.
Due to these weak signals and open protocol, there are two main vulnerabilities of GNSS signals that are jamming and spoofing. This post aims to give a gentle introduction for general audience about spoofing and damages than can be caused by spoofing.
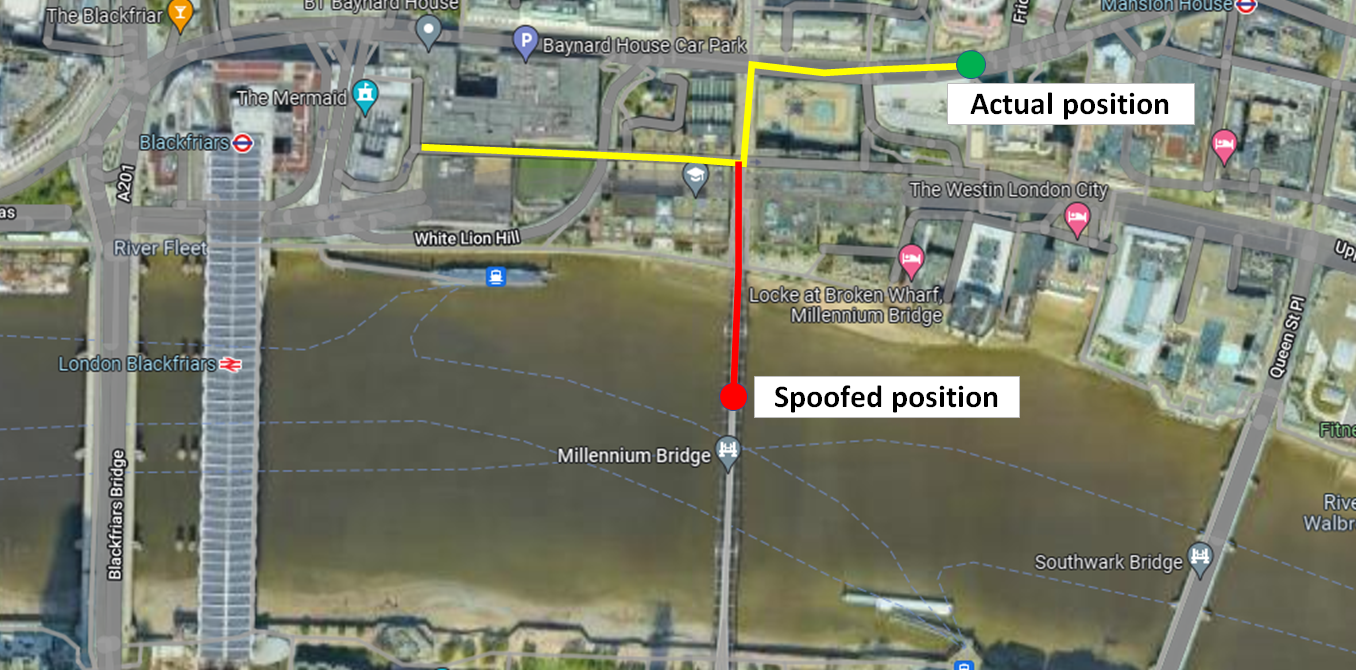
Just for example, there are famous reported cases that clearly show how spoofing work in real life. In one case, it is reported that there is a spoofer that transmit spoofing GNSS signal around a specific area. This spoofing signal were captured by most GPS receivers and the receivers will detect its location is near the airport.
This spoofing attack is used to protect the area from drone attacks. because the GPS on the drones will detect that the drone is near an airport and forces the drones to land (this is a common drone procedure so that all drones should land if they are near or enter an airport area).
Another example is when a military force of a country captured a highly classified drone of another country [6]. Similar as the previous example, a spoofing signal was transmitted to the drone and the GPS on the drone tracked the spoofing signal instead of the authentic signal. The spoofing signal gave false location to the drone so that the drone thought it is at its official base. Then, the drone landed itself not at its true base and, subsequently, being captured.
So, spoofing is a very interesting topic to discuss. Spoofing attack can be used as a defence or to cause damage to a target.
Let us discuss further about spoofing!

Spoofing definition
Spoofing and jamming are classified as signal interference. However, Spoofing is different with jamming.
Spoofing is a type of signal interference where a broadcasted false signal so that a target or victim receiver will acquire the false signal as authentic and derived a false position or velocity or timing information [1,2,3].
In spoofing, the power of the spoofer signal can be similar or little bit lower or higher than the power of the target signal to spoof. However, the spoofing signal characteristics, such as PRN number, should be very close to the authentic signal characteristics [1].
The reason of spoofing attack is difficult to detect is because when a receiver is spoofed (without a jamming attack at the beginning), the receiver is not “aware” or does not know that it has been spoofed and, as such, process the spoofed signals as usual and get false PNT solutions.
Meanwhile, jamming is a type of interference with an intention to cause a victim or target receiver to be disrupted such that the victim receiver cannot produce PNT solutions. A very common jamming attack method is to transmit a high-power continuous or ‘chirping’ (sawtooth pattern) noise signal at the same GNSS frequencies of a victim or target receiver to be jammed.
Since, in jamming, the original or authentic signals are severely disrupted, at least, a receiver will be “aware” that it has been jammed and will not process the jammed signal.
Contrast to jamming, in spoofing, we do not need powerful signal!
Although, there are cases where a spoofer first performs jamming attack to a victim receiver so that the receiver loses track of an authentic GNSS signal and then transmit spoof signals to fool the receiver. But in this case, the receiver will be aware about the situation.
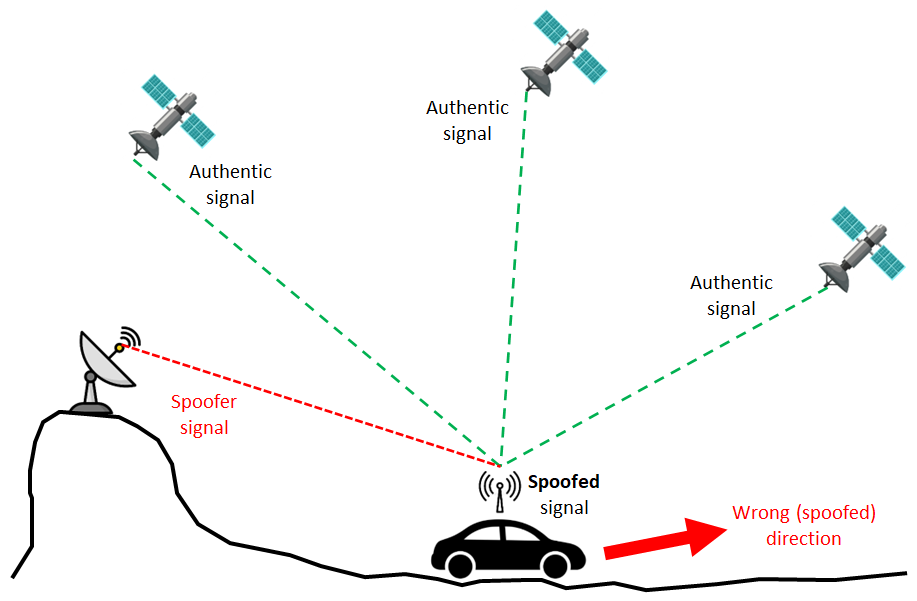
Figure 1 shows the illustration of spoofing attack. A spoofer transmits a false signal at similar power (without jamming attack at the beginning) with a victim/target receiver. Then, this spoofer signal mixed with authentic GNSS signals from satellites.
With various type of spoofing attack methods, the receiver tracks the spoofer signal instead of the authentic signals. since the receiver tracks the spoofer signal, the PNT solutions, such as the direction to go, obtained by the receiver, is wrong.
The basic model of spoofing signal is as follows [1]:
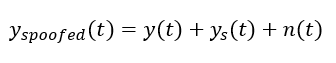
Where $y_{spoofed (t)}$ is the spoofed signal, $y(t)$ is the authentic GNSS signal, $y_{s (t)}$ is the spoofer signal and $n(t)$ is random noise, due to, for example, multipath or other type of GNSS signals within the receiver bandwidth.
The authentic signal (in this case GPS signal) is defined as:
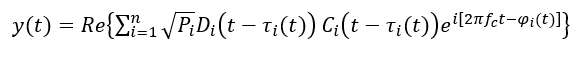
Meanwhile, the spoofer signal is formulated as:
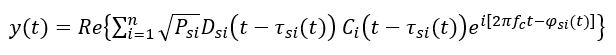
Where:
$i$ is the index of the GPS satellite number $i=1,2,…,32$.
$P_{i}$ and $P_{si}$ are the amplitude of the authentic and spoofer signals, respectively.
$D_{i}$ and $D_{si}$ are the data or message bit of the authentic and spoofer signals, respectively.
$\tau _{i (t)}$ and $\tau _{si (t)}$ are the code delay (due to signal travelling from a satellite to a receiver) of the authentic and spoofer signals, respectively.
$\varphi _{i (t)}$ and $\varphi _{si (t)}$ are the carrier phase noise of the authentic and spoofer signals, respectively.
Spoofing attack
There are various types of spoofing attack, from a low-cost spoofing attack until a sophisticated, but high cost, spoofing attack. Most likely, many spoofing attacks are in the class of low-cost attack.
Some examples of spoofing attack are:
1. Simulated spoofing signal attack
This type of attack is the basic and the easiest spoofing attack to realise.
Basically, an attacker just needs to generate a simulated signal that represent a GNSS signal of a victim receiver that is wanted to be spoofed. The cost for signal simulator is ranging from US$ 0 for an open-source signal generator to US$ 50000 for a high-end commercial signal simulator.
The high-end commercial signal simulator can generate a signal that is close to real situations, that is a signal that have channel impairments due to, ionospheric, tropospheric and multipath effects.
Meanwhile, the low-cost open-source simulator commonly only generates nominal signal that does not representative of rea-world scenario (see the spoofer equation above). Maybe, only some additions of gaussian noise are added on the simulated signal.
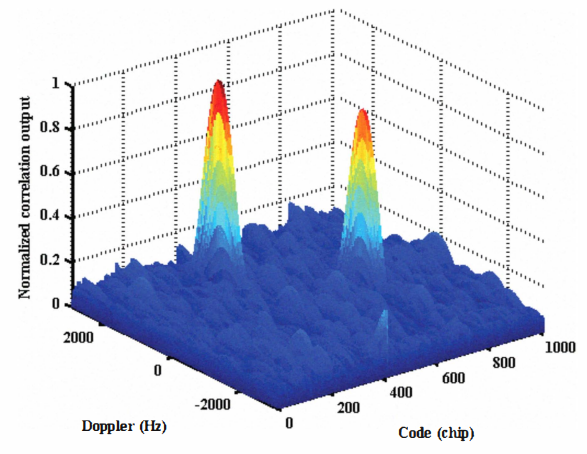
Figure 2 below shows an example when there are two identical GNSS signals (the same PRN or identified from the same satellite). As can be seen, there are two peaks, coming from authentic satellite and spoofer transmitter, in the acquisition search space. A victim receiver can lock the spoofer signal peak instead of the authentic signal peak.
2. Meaconing
Meaconing is also the basic spoofing attack and common in real-world attack [1,5].
In meaconing, an attacker captures a real GNSS signal from its receiver and then re-transmits (replay) the signal, for example, with some delay with its transmitter.
With this meaconing method, the signal resembles a real-world GNSS signal with channel impairments, such as ionospheric delay and phase noise due to multipath. This attack is similar with the previous simulated spoofing signal attack.
Figure 2 above also explains meaconing attack showing two signal peaks from an authentic satellite and spoofer transmitter.
3. Code aligned attack
Code aligned attack is a more advance attack compared to the previous simulated spoofer signal and meaconing attacks.
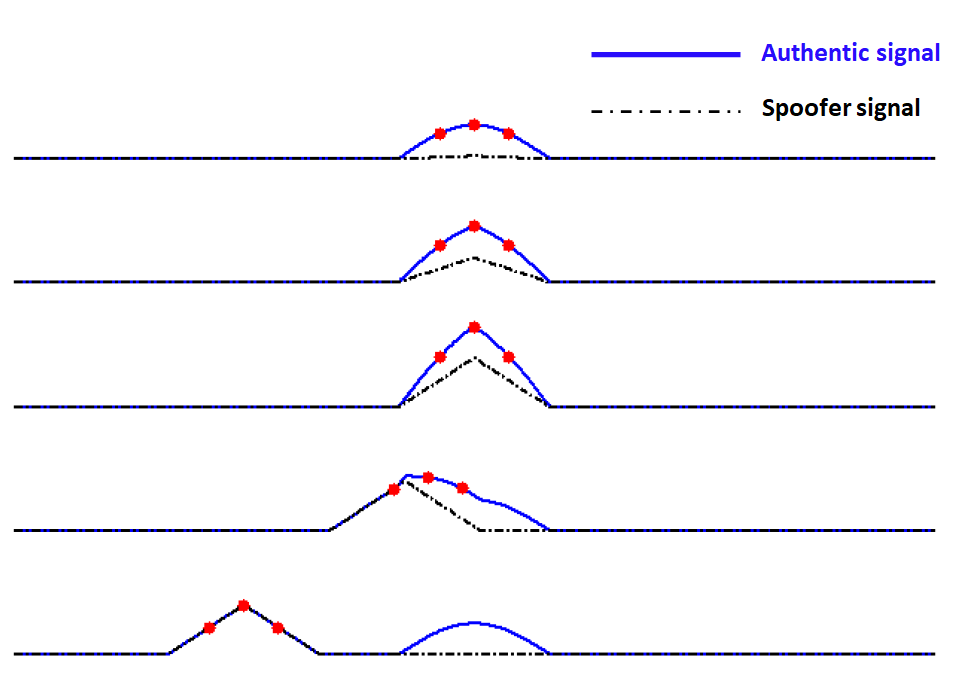
In code aligned attack, the spoofer signal has the same code delay (< 1 chip) and Doppler frequency as in the equations above [1]. Figure 3 below shows the illustration of code aligned attack.
From figure 3, Initially, the spoofer signal amplitude is very low. Slowly, the power of the spoofer signal is increased until it distorts the correlation peak of the authentic signal (blue line). When the correlation peak is distorted, the power of the spoofer signal is slowly increase until the receiver signal processor mistakenly tracks the spoofer signal (black dot).
After the receiver tracks the spoofer signal, then invalid messages will be obtained by the receiver and then a wrong PNT solution can be obtained.
Performing a code-aligned attack is difficult. A lot of expertise and some specified hardware are required to realise a code-aligned attack. Hence, this code-aligned attack will be less encountered in real world than the meaconing and simulated spoofer signal attacks, at least for the moment.
4. Nulling attack
Nulling attack is one of the most sophisticated spoofing attacks. In Nulling attack, an attacker transmits two signals, one spoofer signal with different or “false” information with an authentic signal it wants to spoof and exact copy of the authentic signal, but with 90 degree phase different [1].
The idea of the exact copy of authentic signal with 90 degree phase different is that to null out or removed the authentic signal and then only the spoofer signal remain and is captured by a victim receiver.
Of course, this attack is difficult to realise and is very rare found in real-world situation. At least, more knowledge of the victim’s receiver is required and perhaps, a sophisticated spoofer transmitter is also required.
Spoofing detection
There are methods that can be used to reduce or to defence from spoofing attack by detecting whether spoofing happens or not at a receiver.
Advanced signal processing method
This method is basically the most feasible way to implement at a GNSS receiver. Because this method is based on advanced algorithms and can be implemented on a receiver software. This method processes digital received signal at a GNSS receiver.
A very famous example of this method is receiver autonomous integrity monitoring (RAIM). This method is the oldest and most used spoofing detection method [2]. Examples of RAIM method is by checking the consistency of code delay or Doppler. If the values suddenly drop or increase too large; it can be a sign of spoofing.
Signal-to-noise (SNR) and carrier-to-noise (CN0) ration checking can be implemented. The pattern of these value in normal conditions can be analyse and used as reference of the SNR or CN0 of received signals to be tested.
Statistical-based classifications can be used. Common statistical-based methods for spoofing detection are hypothesis testing and maximum-likelihood ration. These methods require many trainings set to be able to robustly construct the distribution of authentic and spoofed signals. the threshold value for spoofing detection is commonly based on the level of false alarm we want to achieve.
Recently, machine learning methods have been used for spoofing detection, either classical or deep learning methods. For classical machine learning method such as support vector machine and random forest, commonly received raw signals are transformed to extract some features that can be used for training the machine learning model. Meanwhile, deep learning methods can directly use the raw received signal as their model inputs. But, deep learning requires large numbers of training data set and the training process is also challenging.
Cryptographic method
In this method, GNSS messages are encrypted [5]. With this encryption method, only a legitimate receiver has the key to decrypt the message. A spoofer signal most likely does not know what is the contain of the signal and cannot pass the authentication procedure at the legitimate receiver.
However, there are drawbacks of using encrypted messages. For example, the signal complexity becomes higher compared to open GNSS signal without encryption, the data processing at a receiver becomes complex and the require transmission bandwidth will become high due to more data are transmitted.
Correlation with other external timing and IMU sensor
For a receiver that can be connected to an external clock source, it can be used for spoofing detection. For example, when a receiver can be connected to a high-grade external clock source and when the receiver is being spoofed, the detected clock bias can become degrade or outside the specification of the high-grade external clock. This clock-bias degradation can be a sign for spoofing detection.
In case of dynamic receivers, correlating the position obtained from GNSS system with an inertial measurement unit (IMU) sensor can be used for spoofing detection. For example, when the PNT solutions provide a velocity direction that significantly different from the IMU sensor, this situation can be a sign of spoofing.
Radio spectrum and antenna method
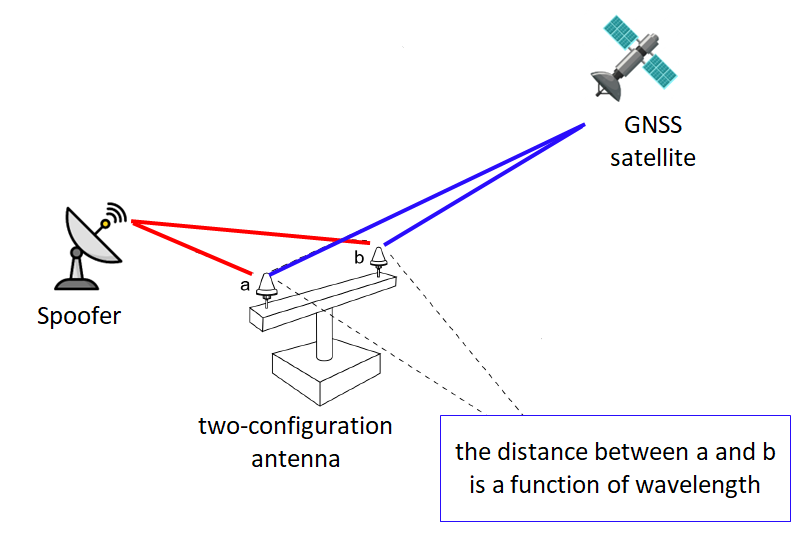
This method requires hardware, that is a special antenna, to detect a spoofing. The antenna usually consists of at least two antennas (RF front-end) with known geometrical relationships with each other, such as the distance between the two antennas.
Figure 3 below shows an example of such antenna. In figure 3, the distance between the two antennas is usually a function of the wavelength of received signals.
The basic idea with this method is that, if we can estimate the angle of arrival of signals at a receiver, we can understand whether the signal is authentic from a GNSS satellite or the signal is from a spoofer.
If the signal angle of arrival is too low, then it can be coming from a spoofer instead from a satellite. Otherwise, if the angle of arrival is large, this signal can be classified as an authentic signal coming from a GNSS satellite.
Spoofing damage
Here are few examples of possible damages caused by spoofing attack in real world condition.
Electricity power generation
A large-scale electricity blackout has happened in Northeast city, Ohio, USA [4]. This black out was caused by a targeted attack of a phasor measurement unit (PMU) used to control electricity power grid. The PMU is a real-time synchronised and high-speed measuring devices to assess the health of electricity grid. The PMU highly depends on precise timing provided by a GPS system. When the GPS signal is spoofed, the timing information will be false and subsequently cause a wrong generator trip and loss of electricity.
Aircraft and flying platform
The process of aircraft landing (and also taking off) is very critical. When the airplane lands, it has to know its vertical height from the ground precisely to be able to safely land.
If the vertical height of the airplane is spoofed, for example, the spoofed vertical height shows the aircraft has a slightly higher height compared to its true height. This false information can cause the aircraft to hit the ground!
However, spoofing an aircraft may also be the hardest attack, since it is difficult to match the Doppler of a fast-flying aircraft and the authentic GNSS signal power received by the plane.
Shipping
An international agreement suggest that a ship with more than 300 ton of weight should carry an automatic identification system (AIS) transponder that transmits the ship’s location from GNSS solutions to the AIS satellite. In real world, some ships, for example fishing vessel wants to spoof itself so that the location send to AIS has a false location showing that the vessel is not fishing in a forbidden water or sea area. A self-spoofing has more advantages than a normal spoofing, because the spoofer knows exactly the characteristic of the receiver to spoof.
Also, for a ship when it wants to approach a harbour, the ship requires to know it location within 8-20 metre of position accuracy. Hence, if the location of the ship is spoofed, it can cause collision between the ship and the harbour.
Trains
A train control management system uses GNSS position and velocity data to manage trains. Of course, when a position of a train is spoofed, it will directly affect the life of the people.
For example, the location of a train is used to determine the portal system in a road crossing. When a train position is false, it can be a situation that a train pass a crossing, but the portal system does not work!
However, many train management systems are equipped with backup positioning system to assure the integrity of their positioning system provided by GNSS satellites.
Taxis and trucks
Many reports show that spoofing on the location of taxis or trucks has been used for intentional purposes. Many cases, taxis or trucks are jammed and spoofed so that the taxi or truck companies cannot track their vehicles.
When taxis or trucks cannot be tracked, the driver of the taxis or trucks can steer their vehicles to unintended or unplanned route. The reasons can be for extra miles to get more money or to steal an expensive cargo and cannot be tracked by the company.
Mobile phone
Actually, spoofing a mobile phone is difficult. Because, the nature of mobile phone is usually it is in a building-cluttered environment and always in motion. It is very difficult to maintain a signal lock on a spoofer signal.
In addition, most cases, the difficulty or the effort to launch a spoofing attack to the mobile phone outweighs the advantage of spoofing the mobile phone.
In mobile phone network, base stations require precise timing provided by GNSS systems. For the case of mobile phone, a GPS jamming (not spoofing) incident has caused a mobile phone signal shortage in San Diego 2007.
Conclusion
Spoofing attack for GNSS signals has been presented in this post. Spoofing is different with jamming.
In Spoofing, the main goal is to fool a receiver so that the receiver extracts false information. Meanwhile, in jamming, the main goal is to cause a receiver to not be able to get PNT solutions from GNSS, for example GPS, satellites.
The threat of spoofing is serious. However, it is also difficult to realise an effective spoofing attack. Hence, it is important to know what spoofing is and also GNSS receivers should also start to equip their receiver with anti-spoofing technologies.
Reference
[1] Psiaki, M.L. and Humphreys, T.E., 2016. GNSS spoofing and detection. Proceedings of the IEEE, 104(6), pp.1258-1270.
[2] Schmidt, D., Radke, K., Camtepe, S., Foo, E. and Ren, M., 2016. A survey and analysis of the GNSS spoofing threat and countermeasures. ACM Computing Surveys (CSUR), 48(4), pp.1-31.
[3] Wu, Z., Zhang, Y., Yang, Y., Liang, C. and Liu, R., 2020. Spoofing and anti-spoofing technologies of global navigation satellite system: A survey. IEEE Access, 8, pp.165444-165496.
[4] Shepard, D.P., Humphreys, T.E. and Fansler, A.A., 2012. Evaluation of the vulnerability of phasor measurement units to GPS spoofing attacks. International Journal of Critical Infrastructure Protection, 5(3-4), pp.146-153.
[5] Caparra, G., Ceccato, S., Laurenti, N. and Cramer, J., 2017, September. Feasibility and limitations of self-spoofing attacks on GNSS signals with message authentication. In Proceedings of the 30th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2017) (pp. 3968-3984).
[6] https://www.wired.com/2011/12/iran-drone-hack-gps/
[7] Broumandan, A., Jafarnia-Jahromi, A., Dehghanian, V., Nielsen, J. and Lachapelle, G., 2012, April. GNSS spoofing detection in handheld receivers based on signal spatial correlation. In Proceedings of the 2012 IEEE/ION Position, Location and Navigation Symposium (pp. 479-487). IEEE.
You may find some interesting items by shopping here.
