Meaconing: the most common type of GNSS spoofing interference attacks
Spoofing attack is a radio frequency (RF) signal interference attack that aims to deceive a global navigation satellite system (GNSS) receiver, such as GPS or GALILEO receiver, so that the receiver track and demodulate the spoofing signals, leading to invalid position, velocity and timing solutions.
Spoofing attack is a radio frequency (RF) signal interference attack that aims to deceive a global navigation satellite system (GNSS) receiver, such as GPS or GALILEO receiver, so that the receiver track and demodulate the spoofing signals, leading to invalid position, velocity and timing solutions.
It turns out that spoofing attacks in most cases are difficult to detect and are more dangerous than jamming attack.
For jamming attack, most likely, a conventional detection method, such as receiver power monitoring in many cases is effective to detect jamming [1]. Another effective and common method for jamming detection on a GNSS receiver is receiver autonomous integrity monitoring (RAIM) [1].
Different from jamming attack, in spoofing attack, most of the time, GNSS receivers are not aware if they are being spoofed. Hence, the receiver continues to process the spoofing signals and subsequently, provide wrong position, velocity and time (PNT) solutions.
Meaconing is the most common type of spoofing attack. Meaconing can be a very simple replay attack or a very advanced spoofing attacks, such as spoofing with aligned code delay and Doppler offset or with cooperative spoofing or with selective-delay, forward-estimation and state-modelling attacks [1].
Let us go into more details!
READ MORE: GNSS spoofing: a fatal attack on GNSS system that is difficult to detect

Attack conditions and GNSS signal models
Meaconing condition
The code delay of the authentic and spoofer signals has a different of more than one chip ($\Delta \tau$ > 1 chip) so that there will be no correlation peak distortion on the acquisition search space.
Signal modelling
The basic model of a perfect authentic and spoofer signals without any channel and hardware impairments are as follow (considering only one satellite signal and one spoofer signal):
- For authentic signal $S_{0}(t)$:
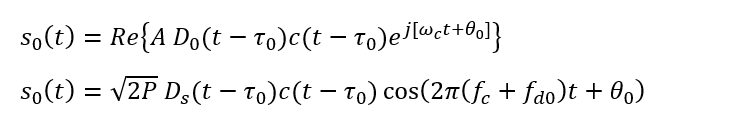
- For spoofer signal $S_{s}(t)$:
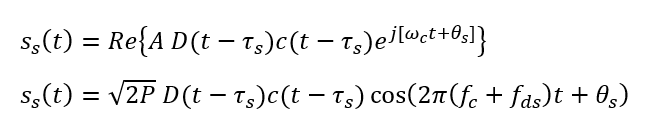
Where:
- $f_{c}$ is the carrier frequency
- $D_{0}()$ and $D_{S}()$ are the data bit for authentic and spoofer signals respectively
- $\theta _{0}$ and $\theta _{S}$ carrier phase for the authentic and spoofer signal respectively
- $c()$ is the PRN code
- $\tau _{0}$ and $\tau _{s}$ are the code delay for authentic and spoofer signal respectively
Hence, the spoofed signal is defined as:
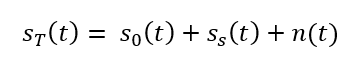
Where $n(t)$ is general noise signal.
It is important to note that, at the RF Front-End until before prompt correlation, the power of the authentic and spoofing signals are buried under the power of noise signal $n(t)$.
READ MORE: GNSS signal modelling considering channel impairments and spoofing interferences
- Global Positioning System: Signals, Measurements, and Performance - an excellent GPS and GNSS book for modelling
Meaconing spoofing attack
The general meaconing can be defined as a type of attack where an attacker or spoofer records an authentic GNSS signal. After recording the authentic signal, the spoofer retransmits the recorded authentic signal to a target receiver to be spoofed.
With this meaconing attack, minimal knowledge of the target receiver, such as geometric distance relationship and channel impairments, are required.
A spoofer that transmits a simulated signal to a target receiver could also be classified in this type of attack.
The general conditions for meaconing attack are as follow:
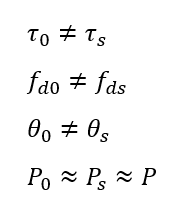
Where:
- Index “0” for authentic signals and index “S” for spoofing signal
- $\tau$ is the code delay
- $f_{d}$ is the Doppler shift
- $\theta$ is the carrier phase
- $P$ is the signal power
From the above conditions, the spoofer only requires the knowledge of the received power at the target receiver so that the spoofer will not transmit too much power so that the receiver can be “aware” if there is an intentional spoofing interference.
Meanwhile, other GNSS observables, such as code delay and Doppler frequency can be different.
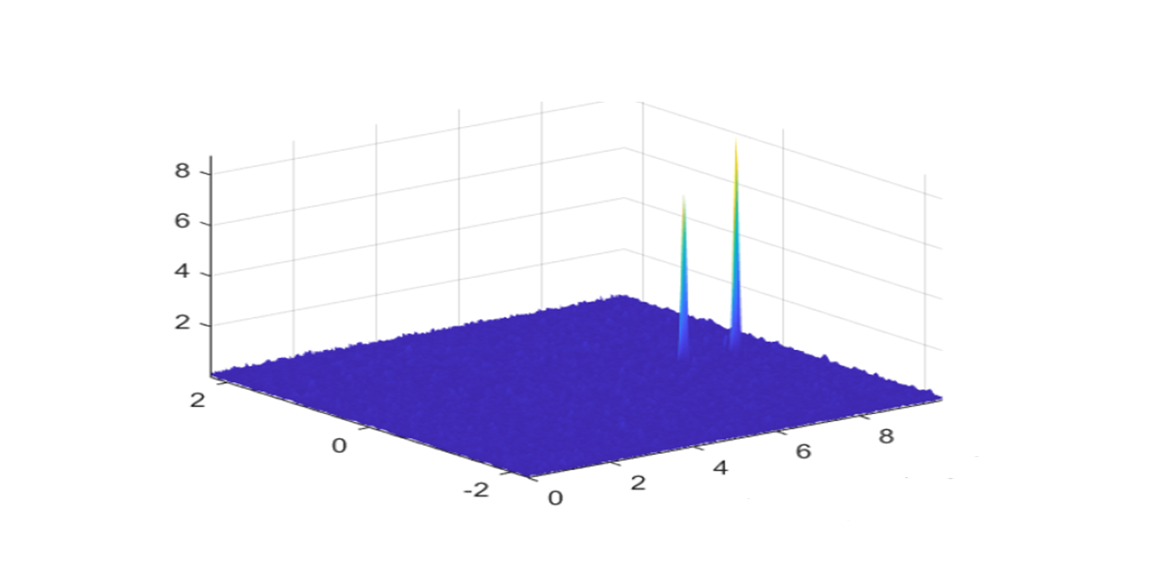
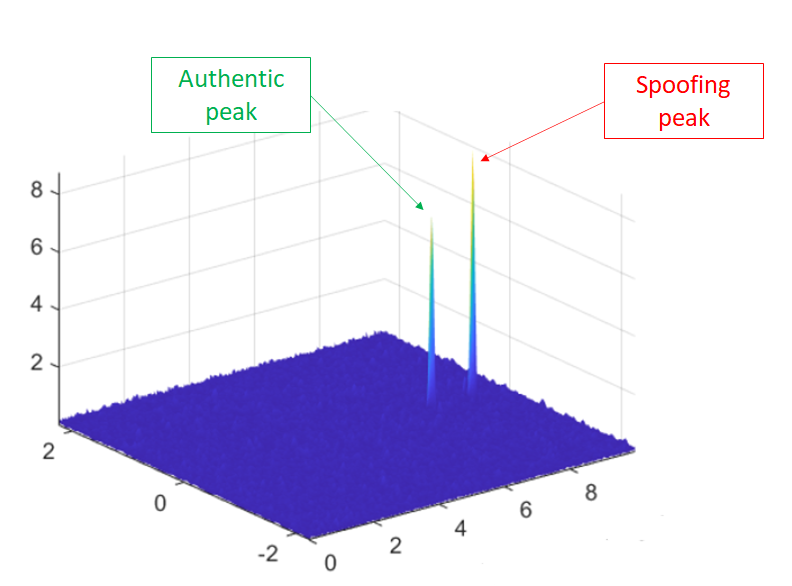
The result of the meaconing attack is that there will be two peaks of signals on the acquisition search space (cross-ambiguity function), one from the authentic satellite and the other from a spoofer, of received GNSS signals.
Figure 1 below shows an example of the acquisition search space under a meaconing attack at a target receiver.
In figure 1, we can observe that the code delay and Doppler frequency between authentic and spoofer signals are different. Meanwhile, the power of the spoofer is slightly higher than the power of the authentic signal coming from a GNSS satellite.
The slightly higher power is to avoid the receiver becomes aware if there is an intentional spoofing interference.
The mathematical model of meaconing attack is as follow.
By defining:
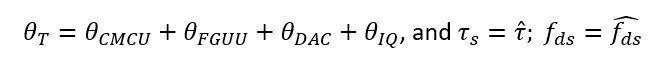
By assuming that the spoofer signal is locked and tracked by the receiver software, the acquisition search space of the spoofed signal (in complex form) is:
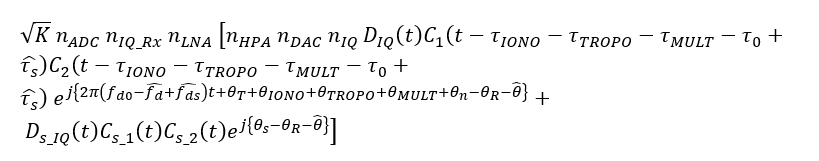
From the equation above, since the software receiver lock and track the spoofing signal (spoofer), the tracked code delay and Doppler frequency are similar or close to the spoofing signal’s code delay and Doppler frequency.
Hence, the component of the spoofer signal become very high (due to match PRN code cross-correlation). Meanwhile, the component of the authentic signals (due to un-match PRN code cross-correlation) becomes minimal and is considered as noise.
In the signal tracking phase of GNSS signal processing chains, after Doppler removal, the spoofed signal are multiplied with the prompt code and is modelled as (in complex form):
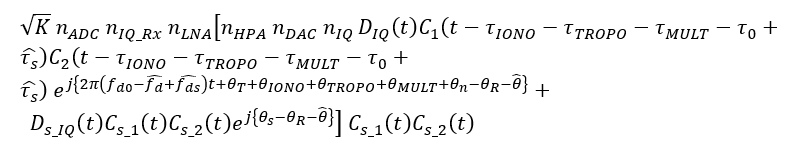
Then, becomes:
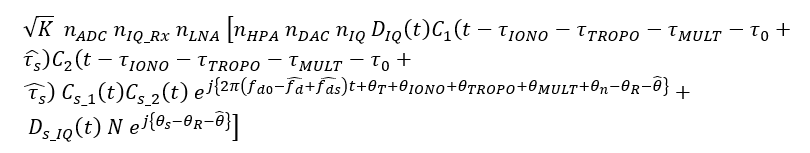
Hence, since the authentic signal component is minimal and the spoofing component becomes large, the spoofed (total) received signal becomes:
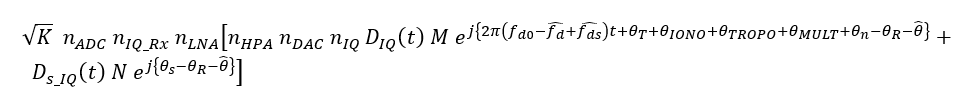
Where:
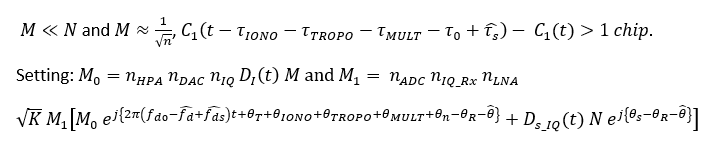
READ MORE: Generating GPS L1 C/A pseudo-random noise (PRN) code with MATLAB and C/C++
- Global Positioning System: Signals, Measurements, and Performance - an excellent GPS and GNSS book for modelling
The effect of a meaconing attack on signal acquisition
In meaconing, an attacker cannot increase the power of the spoofer signal too much higher than the authentic signal.
Because, as being mentioned before, too high power of spoofing signal will change the attack from meaconing to jamming. Jamming attack is considered to be fairly easy to detect as classical signal power detection methods can be applied and, indeed, are already applied by many commercial GNSS receivers.
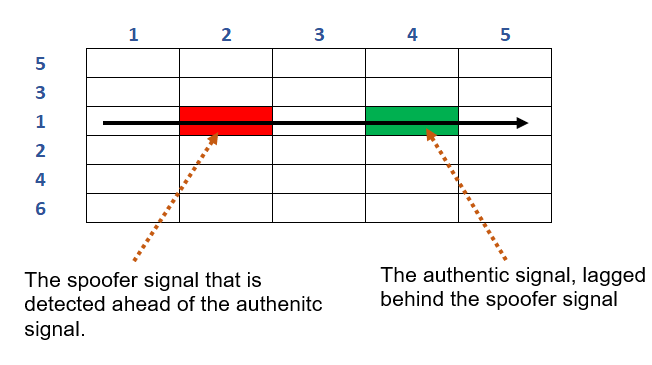
Figure 2 above shows a common search space strategies to find a satellite signal implemented by the software of a receiver.
The searching strategy is sequential until a relevant peak of signal can be detected.
For example, a search can be from the middle of Doppler frequency going through from a small to high code delay value.
Once the signal peak , measured to be above a given noise threshold, is found, the space search process stops.
If the attacker now the software receiver search strategy, for example, the search starts from the small code delay to the high code delay and stops when a signal peak is found.
When this search strategy is known, the attacker can adjust their spoofing signal so that the code delay of the spoofer signal is slightly lower to the authentic signal.
This smaller code delay will cause the peak of the spoofing signal will appear first before the peak of the authentic signal.
Hence, the receiver will first lock to the spoofing signal and then stops the search process.
Eventually, the receiver will progress with the spoofer signals to the tracking and demodulation stage, leading to wrong PNT solutions
The solution of this situation can be by implementing a search strategy that checks the entire search space grid and then locks the appropriate signal peak.
However, this strategy will increase the acquisition time of the receiver.

Limitations of spoofing attack
There are many types of spoofing attack. Meaconing is just one of them, but it can be said to be the most common spoofing attack.
However, implementing spoofing attack is also not easy!
There are limitations to effectively create a spoofing attack. Such limitations are, for example, the target motions, the required cost and labour to perform a spoofing attack, spoofer signal trajectories, security enhancement at a receiver, knowledge to receiver information and characteristics, the attenuation of signal propagation (the inverse squared law) and the duration of the attack.
Detailed discussions for each limitation are as follow:
- The target motions
The motion of a target receiver increases the level of the difficulty for spoofing attack. For example, to be able to constantly maintain the code delay of a spoofer, when there is a small move from the receiver, the code delay and Doppler of the spoofer signal received at the target receiver will change as well. The difficulty will even increase when the receiver motion is high.
- The required cost and labour
It is not easy to estimate the signal power at a target receiver so that an attacker can adjust their spoofer signal power to be slightly higher than a target receiver. Moreover, the transmit signal from a spoofer will degrade rapidly with respect to the distance to the target receiver. This degradation is based on the inverse squared law of signal propagation. In addition, multipath effects will cause the signal degradation becomes more unpredictable. To get all of these information, some labour and their cost are required.
- Spoofer signal trajectories
The ideal condition of a spoofer is to have a line-of-sight (LOS) trajectory between the spoofer and a target receiver. Because most of the time code delay and Doppler estimation are calculated based on a straight-line distance between the spoofer and the target receiver. Any obstacles and multipath between the spoofer and the target receiver will cause the estimation becomes difficult.
- Security enhancement at a receiver
Modern and high-end receivers can have an additional security feature. For example, they can use a special antenna that uses a special radio frequency (RF) shielding on the antenna to block signals coming from unwanted directions. Another example is to use a controlled-radiation pattern (CRPA) antenna that can block spoofer signal from a specific angle of attack or transmission.
- Knowledge to receiver information and characteristics
Very often, an effective spoofing attack requires some knowledge about a target receiver, such as, the receiver power, receiver characteristics, receiver observables and other information. From these requirements, it is very obvious that there should be some degrees of access to the target receiver that, in many situations, are not available.
- The attack duration
A spoofer transmitter should be able to continuously send a match (specifically design code delay, Doppler and other characteristics) signal with an authentic signal so that the spoofer can effectively attack a target receiver. It is difficult to be able to continuously transmit the signal with desired characteristics in a long period of transmission duration. Because any changes at the receiver will significantly affect the required spoofing signal characteristics, such as code delay and power.
READ MORE: Beware of reading signal-to-noise ratio (SNR) from power spectral density (PSD) plot
- Global Positioning System: Signals, Measurements, and Performance - an excellent GPS and GNSS book for modelling
Conclusion
Meaconing is the most common spoofing attack on GNSS signals. In this post, detailed presentation and discussion for the basics of meaconing attack have been presented.
The impact of meaconing attack can be very severe as the spoofing signal (attacked) will deceive a GNSS receiver and force the receiver to track the spoofing signal with wrong navigation-related information signal and provide invalid PNT solutions.
Meaconing attack spans from a simple attack to very complex attack. The simplest meaconing attack is via replaying previously recorded GNSS signals with the addition of some delay. The most difficult meaconing attack is the one that can emulate the real channel impairments as well as aligning the code delay and doppler shift (becoming aligned spoofing attack).
However, although advanced spoofing attacks can be difficult to detect and recover. The realisation of advanced spoofing attacks is also difficult, perhaps, at the moment, is still at theoretical level (although, we may expect the realisation of advanced spoofing attack in near future).
Finally, limitations of spoofing attacks are also presented and discussed.
References
[1] Psiaki, M.L. and Humphreys, T.E., 2016. GNSS spoofing and detection. Proceedings of the IEEE, 104(6), pp.1258-1270.
You may find some interesting items by shopping here.
- Global Positioning System: Signals, Measurements, and Performance - an excellent GPS and GNSS book for modelling